A brief notion of cryptography
To have a better understanding of what it is and how a blockchain works, one must know a few things about cryptography.
Hashes, cryptographic key pairs and digital signatures make the transfer of values in the blockchain possible. When an asset is transferred between wallets, one ‘signs’ a transaction (using their private key), transferring the ownership of a coin (represented by the unspent transaction hash) to the receiving address of the counterpart (in the form of their public key). This article explains these basic concepts of cryptography and information security, which allows for secure communication over the Internet.
Hash
It is the output of a mathematical function that always returns a fixed length sequence regardless of the size of the input.
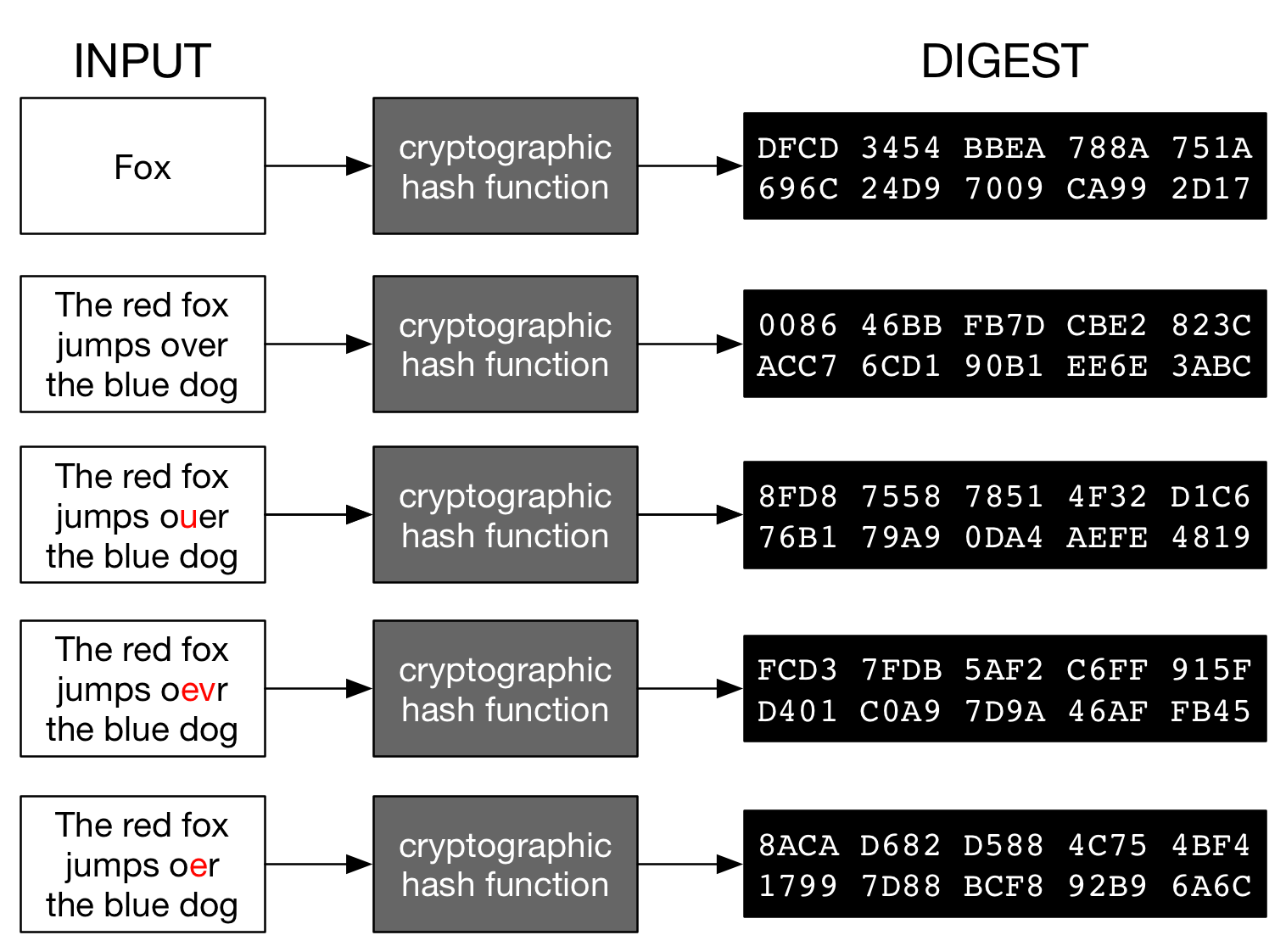
Figure 1 - Cryptographic hash functions - Rebuilt from Wikipedia
Any modification in the input - the text, the length or the order of the characters - will produce a totally different output from what was expected.
Symmetric Cryptography
Symmetric cryptography uses only one key in the whole process: from encryption to decryption. In the next example, the key is called “Alice’s private key” just because Alice was the one that chose it. In this case, the private key is just like a password in a compressed file, for example.
- Alice creates a message
- Alice encrypts the message with a key (a password)
- Alice sends the encrypted message to Bob
- Bob uses the same key (or password) to decrypt the message
- Bob reads the decrypted message
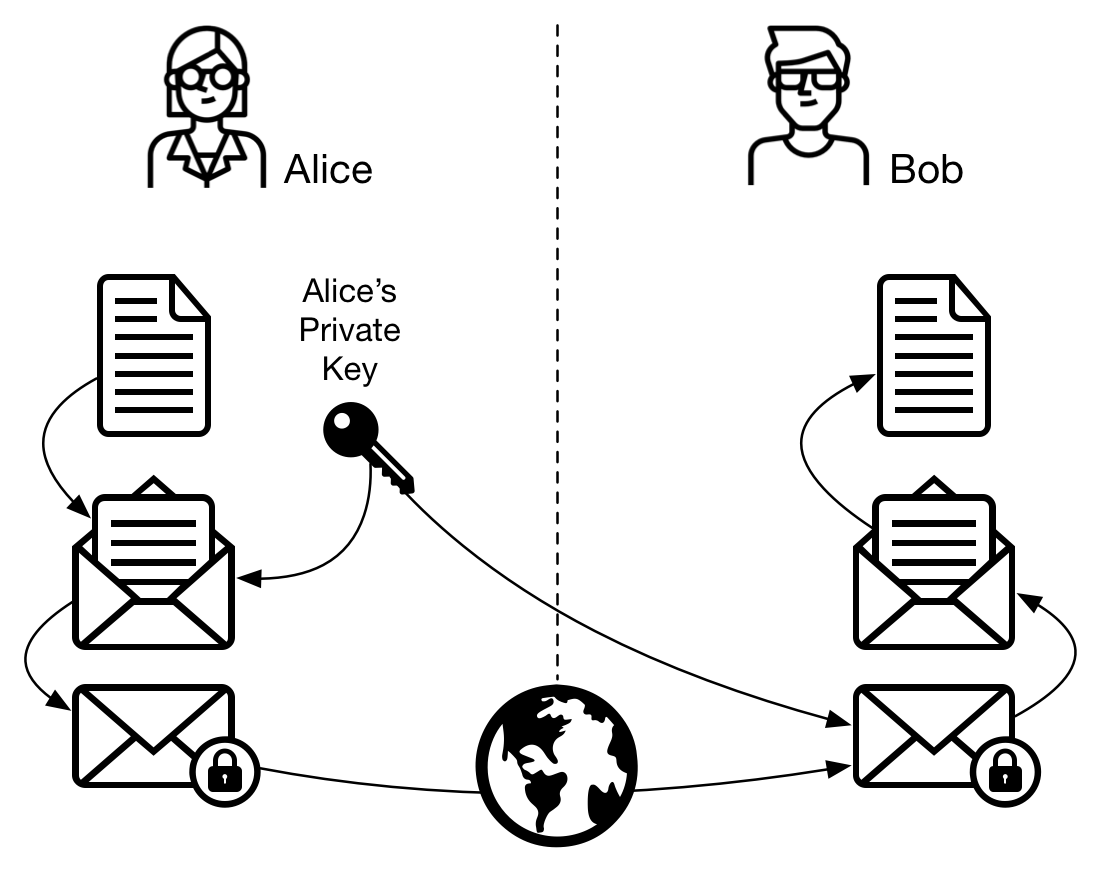
Figure 2 - Symmetric cryptography: Alice sends a message to Bob
The next figure shows a group of 4 users that want to communicate in a secure fashion. One key is generated for every communication channel. For every group member have a unique key with all other individuals, it is necessary to generate a total of 6 keys.
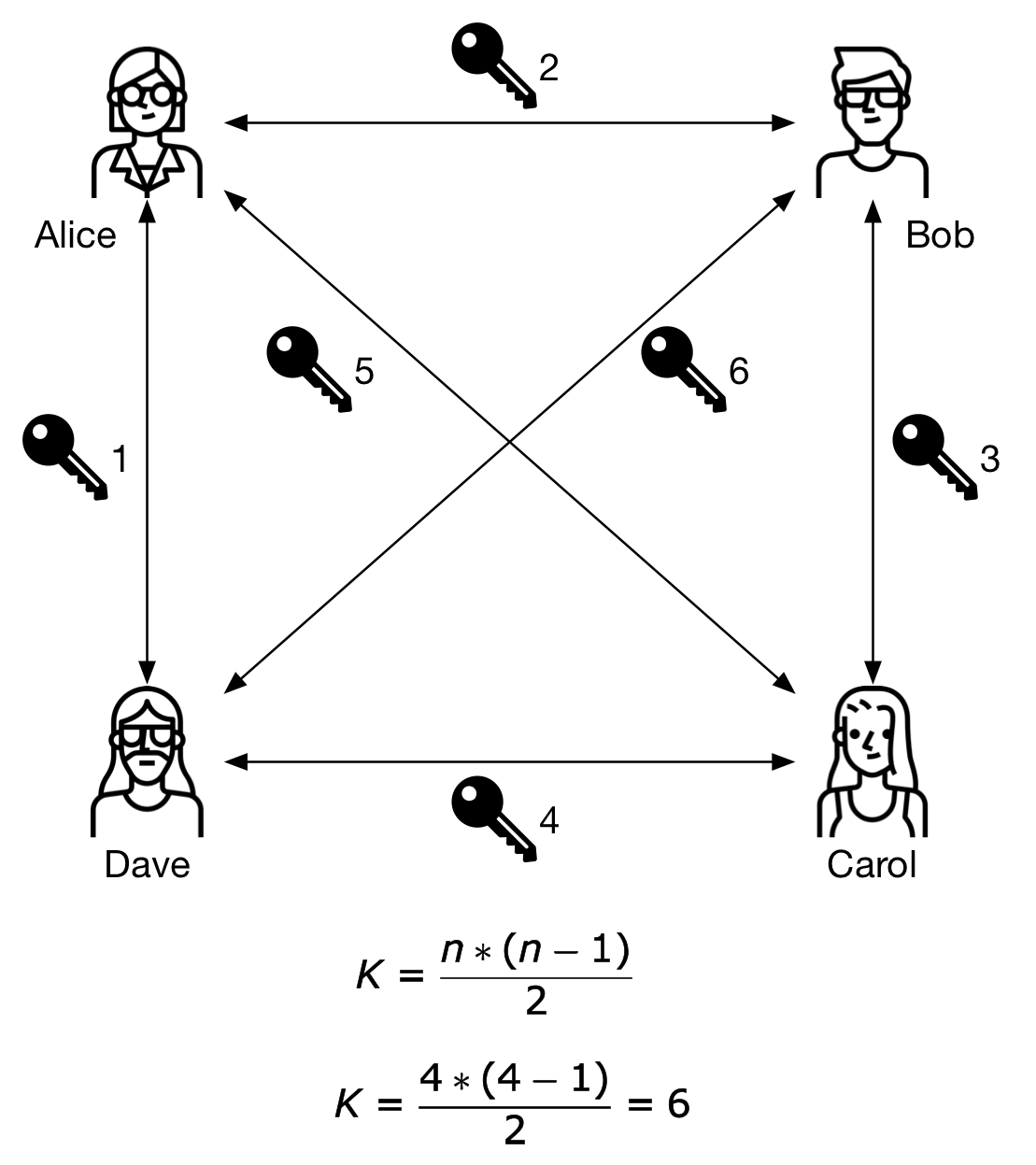
Figure 3 - A small group uses symmetric keys
When every pair of users have their own unique key to protect their communication channel, the number of keys grow exponentially, becoming unmanageable.
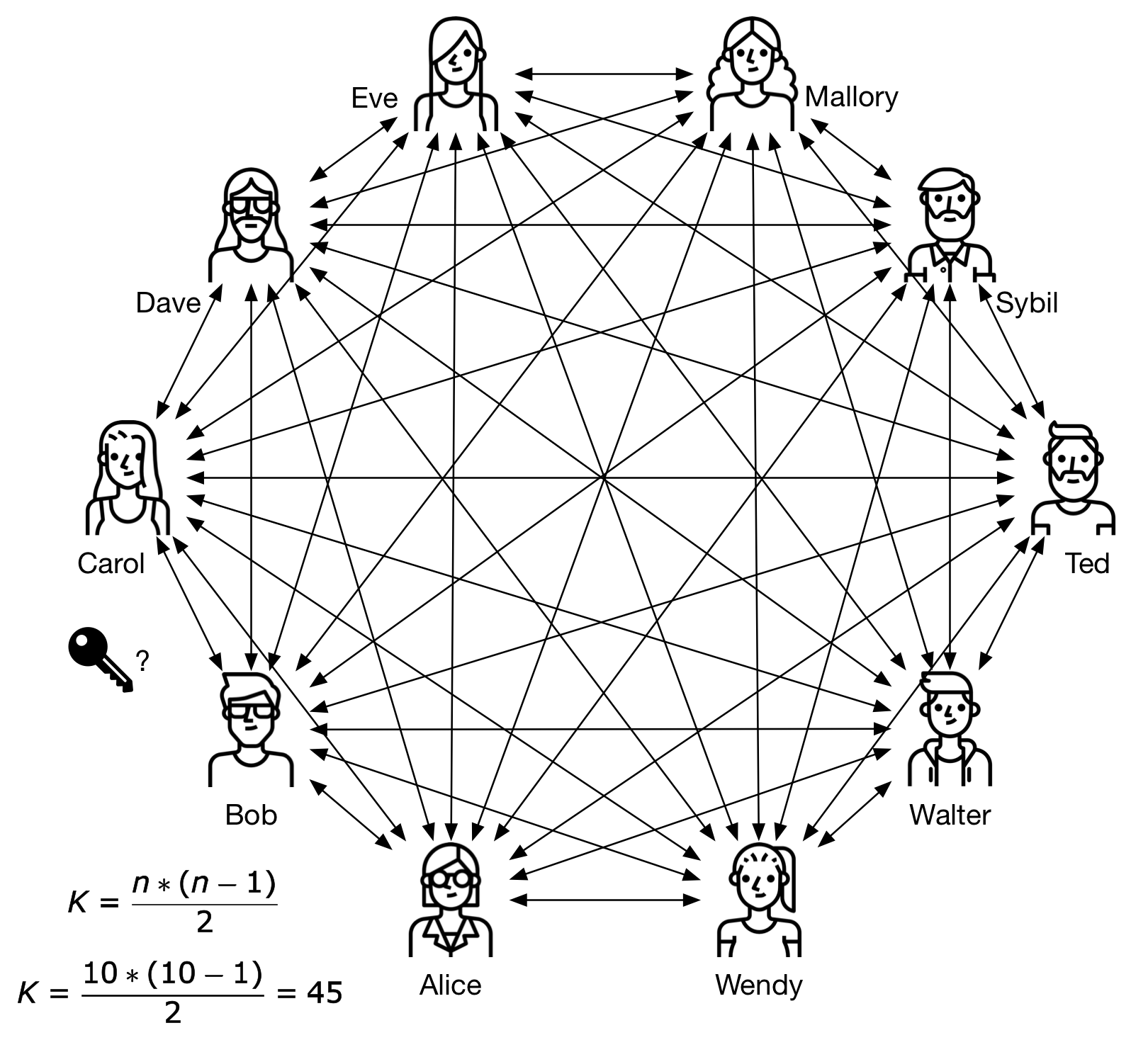
Figure 4 - Exponential growth of necessary symmetric keys
Asymmetric Cryptography
Asymmetric cryptography solves the scalability problem of symmetric cryptography. In this model every user possesses his own key pair. The public key, as the name implies, is public and may be sent to others, and the private key, that must be kept secret.
As seen in figures 6 and 7, the cryptographic operation is always performed with both keys from the same key pair: what is started with the private key is finished with the public key from the same pair, depending on the operation.
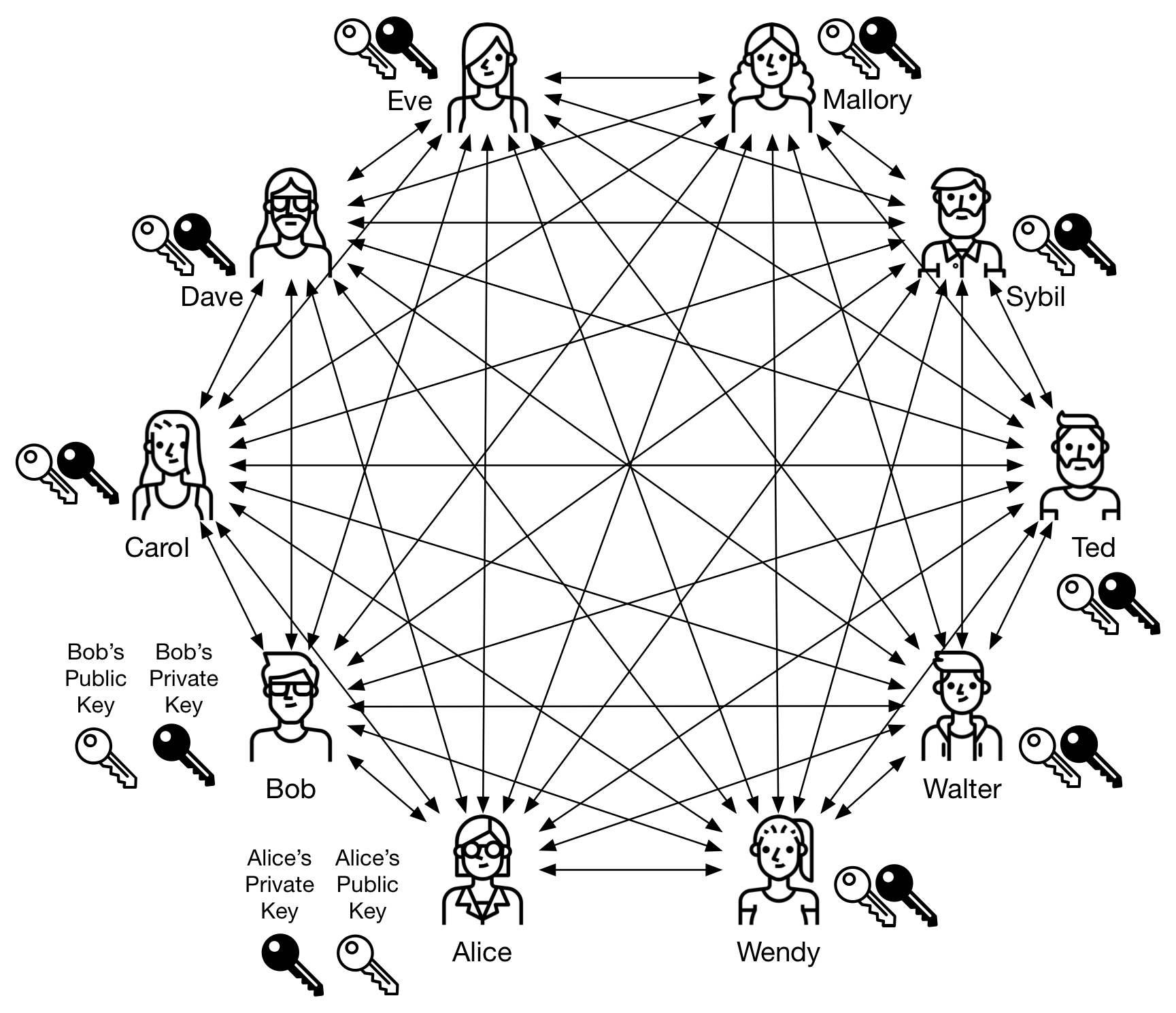
Figure 5 - Asymmetric cryptography: each user has its own key pair
While in symmetric cryptography the sender chooses the key or password to be used, in asymmetric cryptography the keys will be the receiver’s. Receiver’s public key, which is publicly available, is used to encrypt the message. The private key, which only the receiver has, will be used to decrypt the message. This way everyone can send encrypted messages to the receiver, and the receiver is the only one that can read these messages.
- Alice creates a message
- Alice imports or receives Bob’s public key
- Alice encrypts the message with Bob’s public key
- Alice sends the encrypted message to Bob
- Bob uses his private key to decrypt the message
- Bob reads the decrypted message
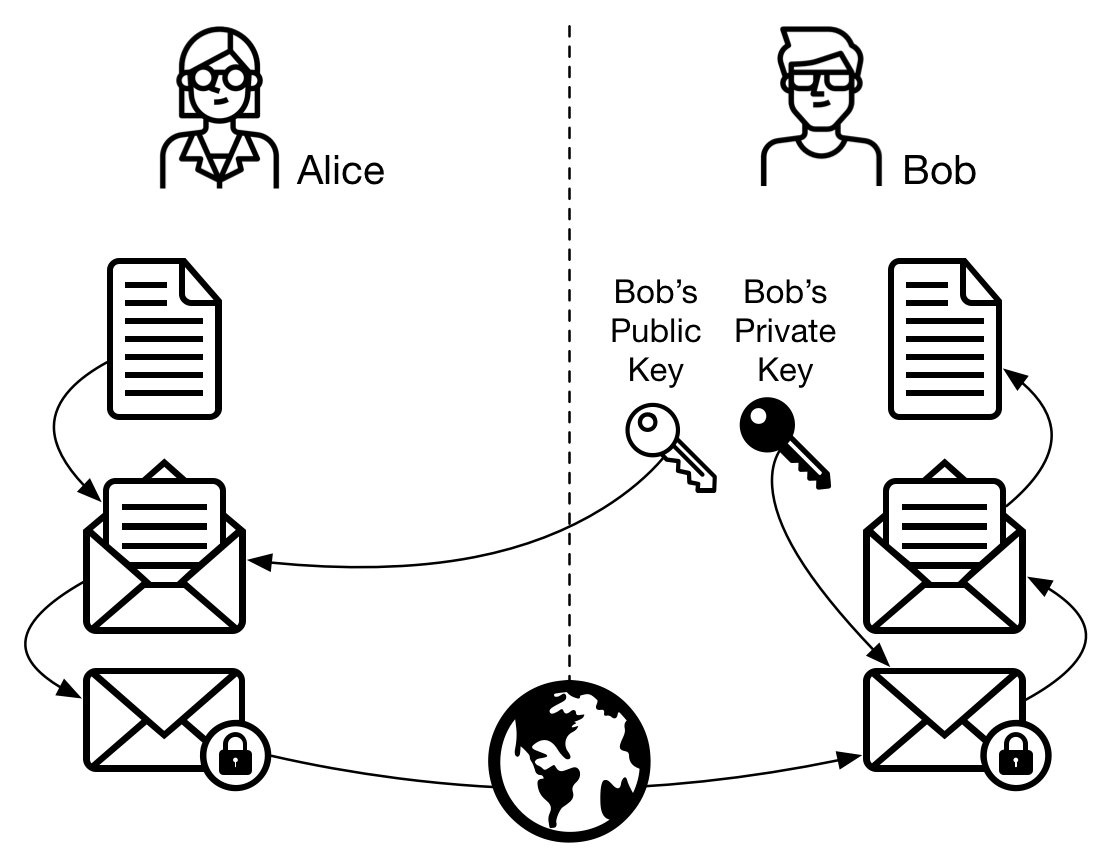
Figure 6 - Asymmetric cryptography: Alice sends a message to Bob
Digital Signature
Digital signature is the process of making sure a message wasn’t modified by an unauthorized user while stored or in transit. In a PKI model, as shown in figure 8, a digital signature is also used to ensure non-repudiation, which means a user won’t be able to deny signing the message. In a structure without digital certificates, it is only possible to determine that a certain private key was used to sign the message, because the message was validated using a public key from the same pair.
- Alice creates a message
- The digital signature function generates a hash of the message
- Alice’s private key is used to encrypt the hash
- The encrypted hash is attached to the message
- The message is sent to Bob
- Bob receives the message
- The verification function generates a new hash of the message
- Alice’s public key is imported, in case it hasn’t been yet
- Alice’s public key is used to decrypt the hash attached to the message
- Both hashes are compared
- If the hashes are identical Bob knows the message hasn’t been tampered with; otherwise Bob considers the message compromised and discards it
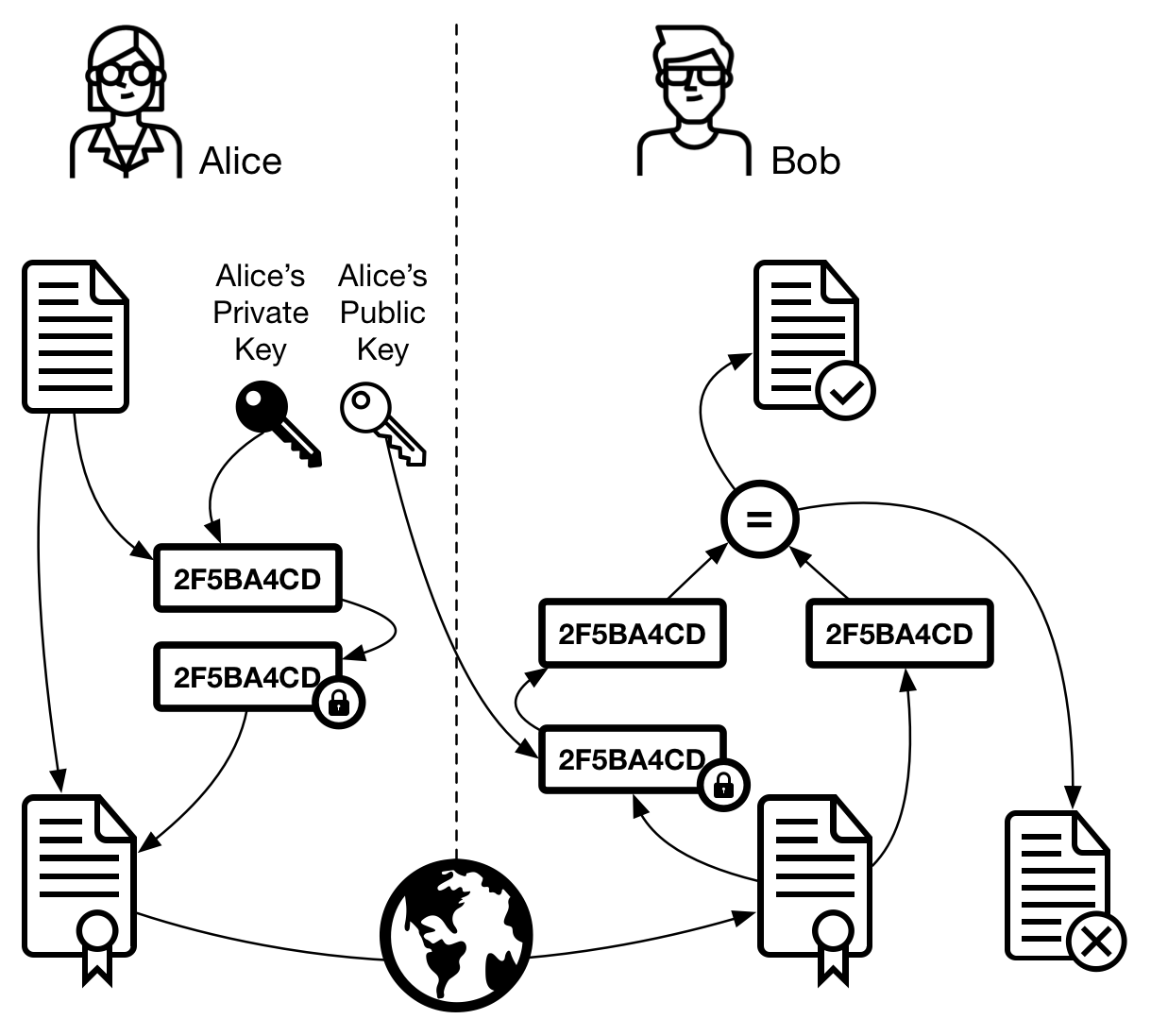
Figure 7 - Digital signature: Alice sends a signed message to Bob
Centralization vs Decentralization
In a centralized structure there are digital certificate issuing servers, like the Certificate Authority, for example. Digital certificates may be used to identify users through documents previously presented and to connect a user to a public key, since all public key look alike.
Public Key Infrastructures, as shown next, may enforce a backup of user’s keys to avoid information loss due to accidents or users leaving the company. This is a well-known security control.
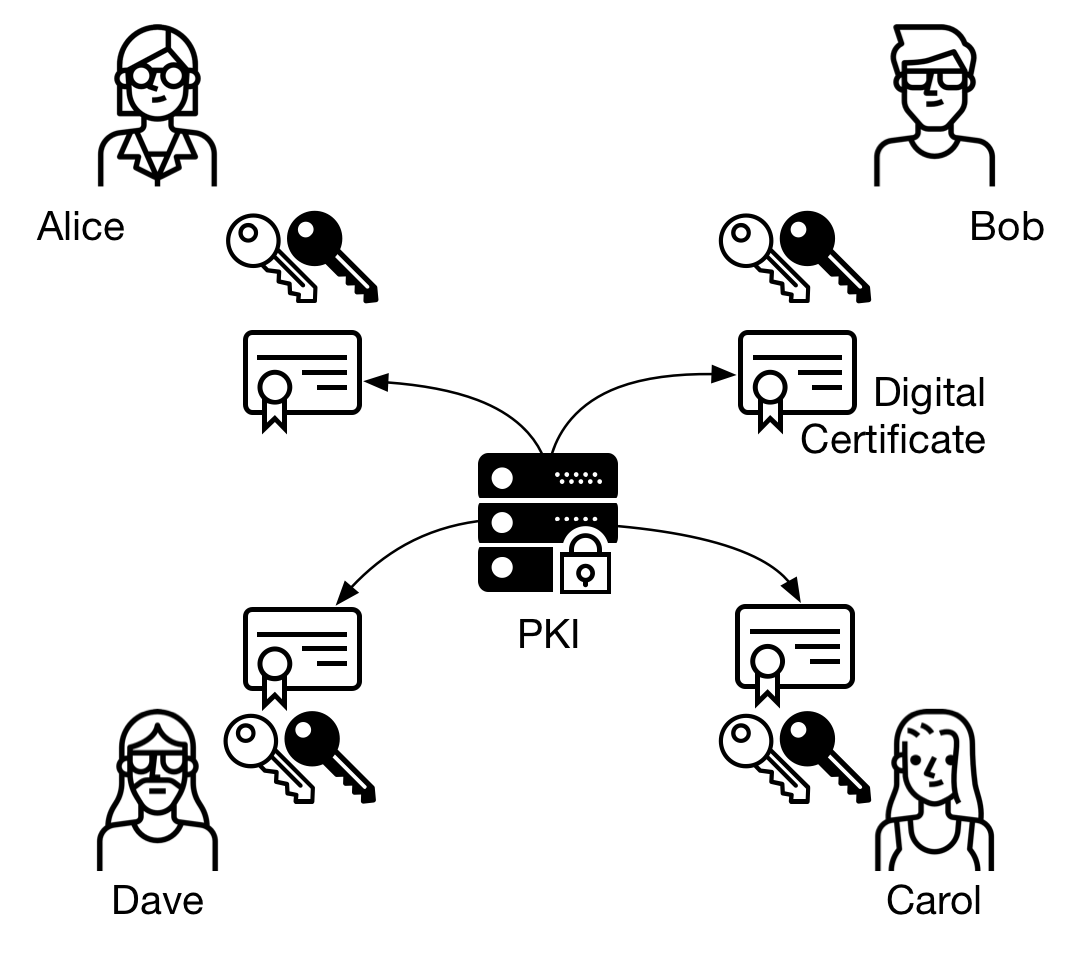
Figure 8 - PKI (Public Key Infrastructure) example
Most digital currencies are decentralized. There is no central entity to identify users and generate digital certificates. Their model resembles PGP. Conversely, there is no backup for user’s keys. This is why it is paramount to backup the private key, or seed, which is the mnemonic representation of the private key.
Cryptoassets
Digital currency, or cryptoassets, uses the concepts shown here. Understanding these concepts is important to understand how blockchain technologies work.